First posted 11/20/2022
As always, opinions in this post are solely those of my own, and not necessarily those of any organization I am currently affiliated with or have been in the past.
Due to a certain mandate from Uncle Sam, I’ve been doing a lot more IPv6-only stuff than I ever was expecting to do in 2022. However, I often hear things like “Oh Tom, Department of Veterans Affairs still has Windows XP machines hooked up to medical devices in their hospitals, no way can they do IPv6-only. Why should any other federal institution bother with IPv6? Did we run out of IT modernization projects that make daily operations easier or more secure?” Normally I’m all about saying things like “well IPv6 is a great change agent to part ways with technical debt, don’t fight the fed, IPv6-only really isn’t the beast you think it is. Maybe this another good thing to help ditch obsolete infrastructure.” But just for fun, I wanted to see if I could get Twitter working on an ancient IPv6-only laptop running everyone’s favorite 21 year old operating system: Windows XP. Much to my surprise, you can successfully do this thanks to a nifty band-aid with ncat, so let’s dive right in to some questionable ideas on a tremendously end of life operating system!
Step 1: Get an ancient Windows XP machine (or VM), install prerequisites
Obtaining a machine with Windows XP on it isn’t as easy as it was a decade ago; you’ll either need to find someone with an old Windows XP ISO + working CD key or buy something used on Amazon or eBay. Fortunately, I’ve been holding on to an old IBM T23 laptop for over a decade because it has a built-in serial port, which has been real helpful as I’m always losing USB to Serial adapters around the house. It only has 256mb RAM, but it can still run a web browser that’s still maintained like K-meleon. All of the “household name web browsers” stopped supporting Windows XP years ago, so you’ll want to install K-meleon browser or similar. Otherwise all the fancy new flavors of certificates, TLS, Javascript, etc. used on web pages in the 2020’s have no chance of working on WinXP web browsers from the past.
Once you get a modern web browser installed, you’ll also need to install a version of Nmap suite that still runs on Windows XP. According to secwiki, the final version for this is Nmap 6.47, which is available to download on their website. We only need the ncat tool to workaround WinXP’s IPv6 DNS resolving limitations, but I usually install the full Nmap suite since you never know when their other tools might be helpful.
Step 2: Make sure you have a known-good DNS64/NAT64 setup so IPv6-only internet browsing isn’t miserable
If you plan on getting your Windows XP machine to access IPv4-only websites like Twitter, you’re going to need a known-good IPv6-only environment with the various transitional tools to allow devices without IPv4 addresses to reach IPv4 webservers. My home ISP doesn’t do IPv6 yet, which is a bit frustrating as I had to jump through extra hoops with tunnelbroker.net for getting an IPv6-only DNS64/NAT64 environment working. You’ll find all the steps I did for this at https://kd9cpb.com/nat64, but just about any other blog out there about DNS64/NAT64 will do.
Alternatively, you could use an HTTP/HTTPS proxy server instead of DNS64/NAT64 to access IPv4-only websites from IPv6-only Windows XP, but I chose not to go down that path. I’d also recommend getting your DNS64/NAT64 IPv6-only environment fully tested with a more modern OS before you start tinkering with WinXP IPv6-only: there’s way more resources for IPv6-only troubleshooting with Win10 on the interwebs.
Lastly, it’s helpful to have the IPv6 subnet which your WinXP machine will be located on to support SLAAC addressing. I’ve heard mixed reviews about other methods of IPv6 addressing (ie DHCPv6 or static) actually working in WinXP, and to be honest I don’t want to spend time tinkering with anything other than SLAAC at this time. If you end up trying this at home with DHCPv6 or static addressing, please let me know in the comments. Per https://ipv6int.net/systems/windows_xp-ipv6.html, it seems like this can be an uphill battle.
Step 3: Install IPv6 protocol on the WinXP machine, ensure you can ping Cloudflare’s DNS64 servers
You’ll need to install the IPv6 protocol from adapter settings in WinXP, fortunately there’s good blog posts over at Ghacks.net (from over 10 years ago!) and TechRepublic (from over 20 years ago!) which walk you through this step-by-step. I ended up doing a combination between both of those posts on my laptop, here’s the exact things I did to get a SLAAC address and corresponding default route on WinXP:
- Install IPv6 as a network protocol from control panel’s network adapter settings “add” button per the Ghacks.net article
- Open up a command prompt, run the command “ipv6 install” (This might not be necessary if you add IPv6 via control panel, but I did it for good measure anyways)
- Do an “ipconfig /all” to ensure you pulled a global IPv6 address from your IPv6-only network
- Set a bogus static IPv4 address on your network adapter to ensure you’re living the IPv6-only dream. Set the DNS server to 127.0.0.1; this is important for the next step.
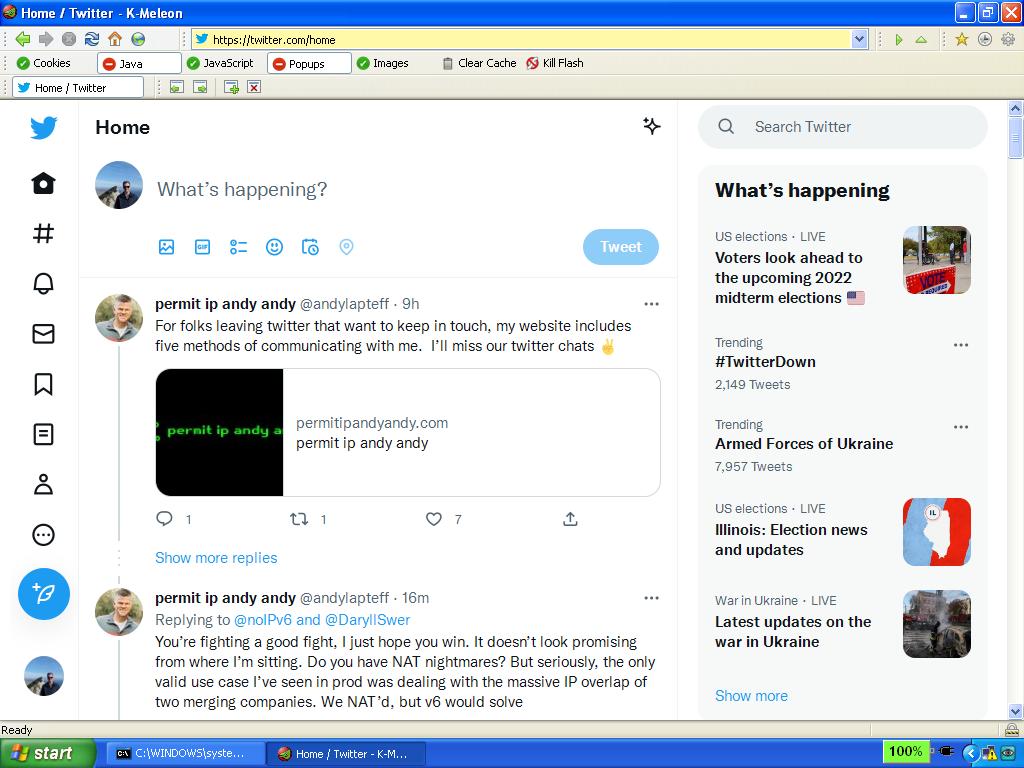
If all goes well, you should now be able to ping Cloudflare’s DNS64 servers at 2606:4700:4700::64 and 2606:4700:4700::6400.
Step 4: Use Ncat to work around WinXP’s lack of IPv6-only DNS Resolving capabilities
Thanks to @agowa338 on Twitter, it was pointed out to me that you can use good ‘ol netcat to redirect DNS traffic from WinXP into an IPv6-only DNS server. This is a big deal because without the following ncat trick, WinXP has no capabilities of hitting a DNS server via IPv6, only IPv4 is supported. Sadly, if you close netcat, your WinXP machine will lose its ability to reach DNS servers, therefore I would not recommend actually doing this on a production-critical machine (not that anyone would be running WinXP on a prod-critical system in 2022, right?!?). But if you’re really in a jam or just homelabbing, go ahead and run the following from command prompt to forward DNS traffic into Cloudflare DNS64:
ncat -k -l -u 127.0.0.1 53 -e "ncat -u 2606:4700:4700::64 53"Step 5: Surf the web without IPv4 on Windows XP!
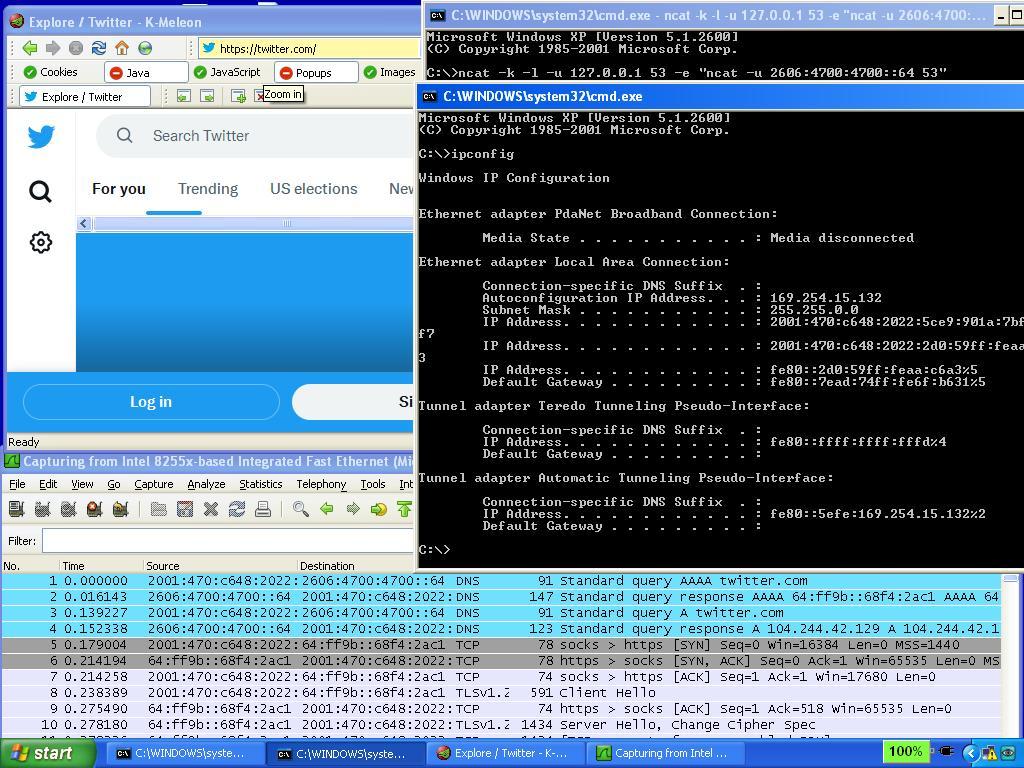
If all went well, start up K-meleon browser, you should be able to browse the web with ease, or at least until running out of RAM if you’re on an early 2000’s machine:
We can see that our DNS forwarder is working well given the DNS traffic at the top of a Wireshark capture showing the flows, and HTTPS web surfing works well as K-meleon has more recent SSL & Root Certificate stuff. Sadly my T23 laptop only has 256mb of RAM, so it didn’t take very long before the machine came to a screeching halt when I ate up all the memory trying to load Twitter. I wasn’t able to actually send a tweet out, but it did load up the timeline just fine, so I think a newer machine (or VM) running WinXP would be actually usable:
Step 6: Disconnect your Windows XP machine and never connect it to the internet again. Ever. Full stop.
I’m sure there will be at least one mean tweet coming my way when I share this write-up saying “OMG WinXP is broken beyond repair when it comes to information security, this is such a bad idea! You’re going to get hacked immediately!” To be fair, the WinXP haters are totally right, this is a terrible idea security-wise, and you really shouldn’t attempt to use WinXP for websurfing anymore. The whole point of this homelab is to prove even a 21 year old operating system can do IPv6-only, so getting your latest fully patched version of Windows to talk IPv6-only might not be as difficult as you think. But just because you can do this, doesn’t mean you should…
Windows XP is sentimental for me as it was quite literally the OS I grew up with. From junior high all the way through college (2002-2012), I spent countless hours using it. Sure, towards the start of the 2010’s I’d start using Windows 7, but I sure made a lot of money repairing Windows XP machines as a teenager. Nowadays things are way more secure and the computer repair field is a fraction of what it used to be. I’m glad that’s the case; computers should be way easier to use & less likely to attract malware in 2022 than they were in 2002, but there’s times when I miss the simpler pre-smartphone revolution days of IT circa 2008.
Regardless of whether WinXP was something that you dealt with as part of your career many years ago, or if WinXP was released before you were born, I think we can all agree that it’s played a big role in how we think about desktop computing today. While WinXP still sparks joy for me on occasion (like using it to play some original Halo, Unreal Tournament 2004 or other classic game offline), it simply shouldn’t be used for anything business related anymore, and it shouldn’t be used on the internet in 2022. Full stop.
I hope you’ve found this homelab entertaining, I hope more people give IPv6-only a try, and I truly hope nobody does this IPv6-only WinXP + ncat trick to keep technical debt around longer than necessary at their organization 🙂
You’ve reached the end of the post! Click here to go back to the list of all Homelab posts.
You should also know I use Amazon Affiliate links to defray the cost of otherwise ad-free webhosting


Interesting project.
You may want to look into `socat` rather than netcat. socat is designed to do networking transformations while being in the middle of a network connection, where as netcat is more designed to be at a connection termination.
Thanks Craig!
I’ll have to check that out soon, I probably should be using socat more often for other things too
I’ve gotten this working without ncat by replacing nslookup with the one from server 2003,then configuring DNS servers via netsh int ipv6 add dns. Server 2003 supports DNS over v6, it’s only XP that doesn’t. I’ve also gotten IPv6(though not v6 only) to work in NT4 by installing an experimental stack-msripv6 to be precise.
That’s fantastic! Never thought about taking nslookup from server 2k3, great find